Sudo for Windows is a new feature that was introduced in Windows 11 Insider Preview Build 26052. It allows users to run elevated commands directly from an unelevated console session, similar to how sudo works on other operating systems. Sudo for Windows is an ergonomic and familiar solution for users who want to elevate a command without having to first open a new elevated console. It also preserves the user’s profile and ownership of created objects. Sudo for Windows is an open-source project that can be found on GitHub.
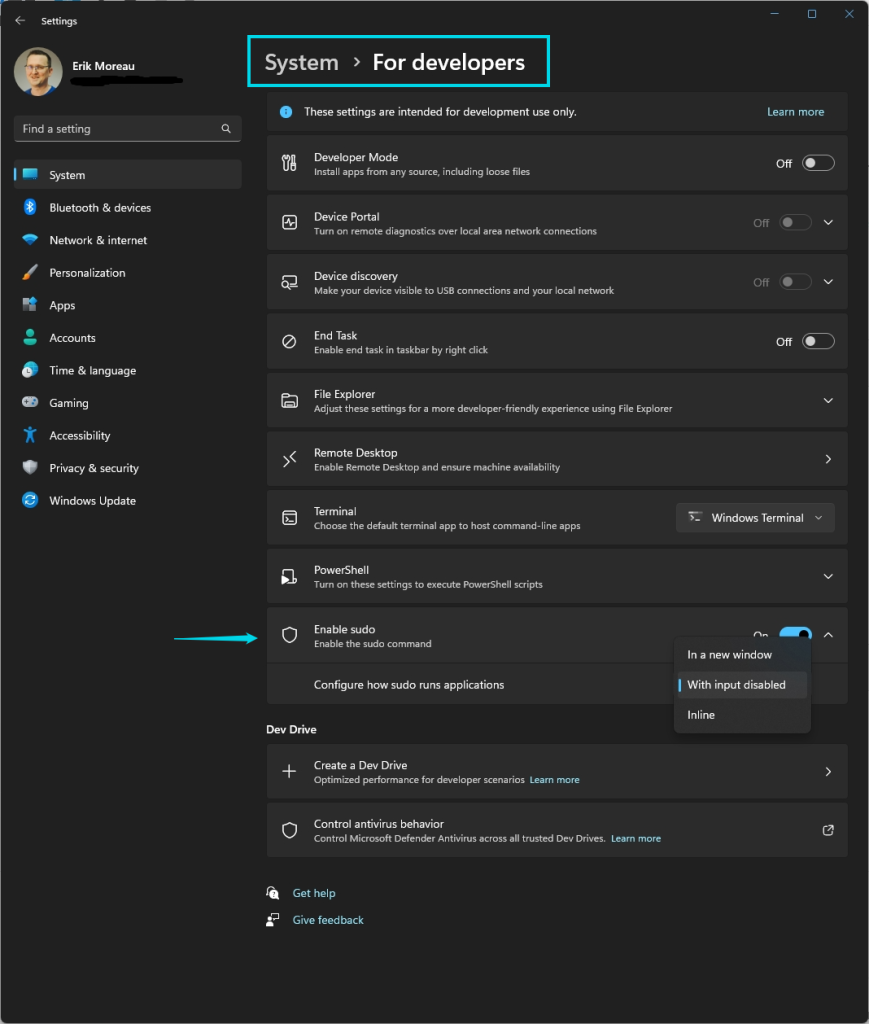
To enable Sudo for Windows, you need to navigate to the Settings > For Developers page in Windows Settings and toggle on the “Enable Sudo” option.
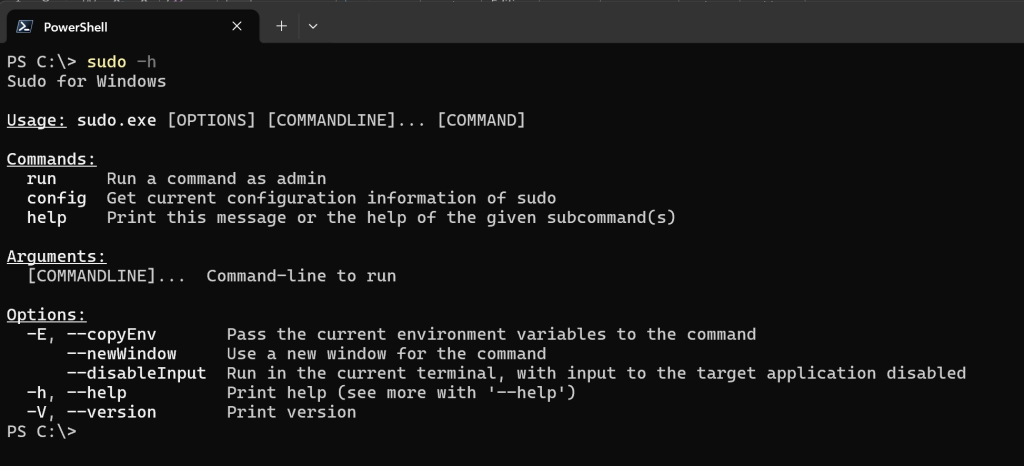
You can also enable Sudo for Windows by running the following command in an elevated console session:
sudo config --enable <configuration_option>
Sudo for Windows currently supports three different configuration options:
- In a new window (
forceNewWindow): This is the default option. It opens a new elevated console window and runs the command in that window. - Input closed (
disableInput): This option runs the elevated process in the current window, but the new process will not accept any user input. This option is useful for processes that do not require further user input after elevation. - Inline (
normal): This option is most similar to the behavior of sudo on other operating systems. It runs the elevated process in the current window. This option is useful for processes that can take in input and route output to the current window.
To change the configuration option, you can use the drop-down menu in the Settings > For Developers page in Windows Settings, or run the following command in an elevated console session:
sudo config --enable <configuration_option>
When elevating a process from the command-line with sudo, a UAC dialog will appear asking the user to confirm the elevation. Once the user confirms the elevation, the process will be elevated based on the configuration option selected by the user.
The advantage of Sudo for Windows is that it provides a consistent and convenient way to run elevated commands from the same console session.
Keep in mind however, the main security risk is that malicious processes could try to hijack the elevated process using the connection established by sudo. This risk is higher when using the Input closed or Inline configurations, as the elevated process can receive input from the current console window. Therefore, users should be cautious and understand the implications before choosing their configuration option.
Enjoy testing with SUDO!